How Zero-Day Exploits Are Driving Cybersecurity Breach Trends
How unknown flaws are fueling modern cyberattacks and shaping defenses
Zero‑day exploits are reshaping the cyber threat landscape. These vulnerabilities are unknown to defenders until after attackers exploit them. In recent years their frequency and sophistication have surged, reshaping breach trends across sectors.
What is a zero-day?
A zero-day vulnerability is a flaw in software or hardware that the vendor does not yet know about, which means there is no patch or fix available. When attackers find and exploit it before it can be repaired, it is called a zero-day exploit. The name comes from the fact that defenders have had “zero days” to prepare a fix.
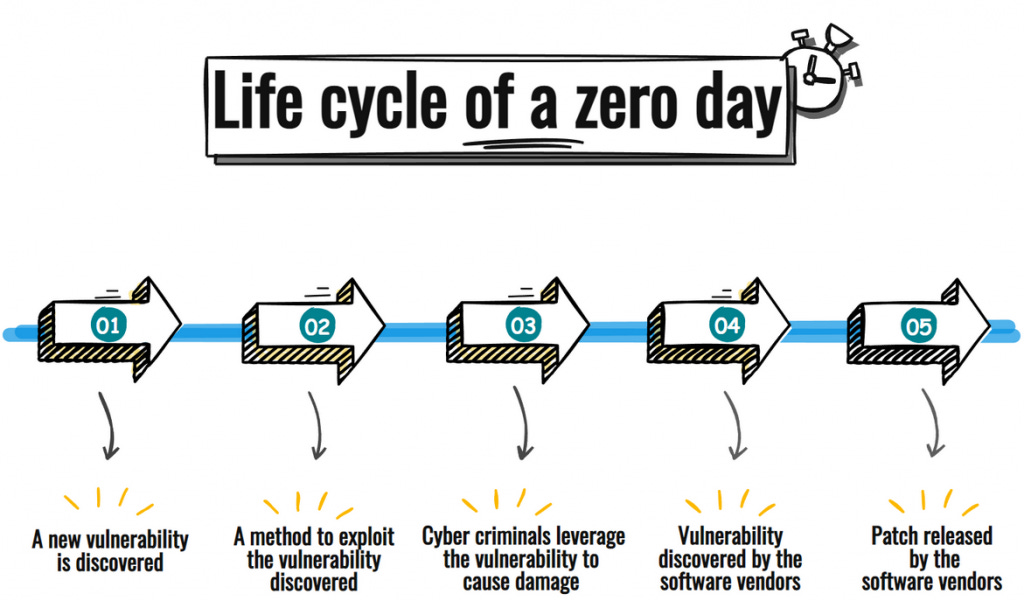
The life cycle of a zero-day usually follows these steps:
A vulnerability is discovered.
An attacker develops a method to exploit it.
Other attackers may begin to use the exploit for damage or profit.
The vendor eventually discovers the flaw.
A patch or update is created and released.
Users apply the fix to secure their systems.
Until that patch is deployed, systems remain exposed, which is why zero-days are considered some of the most dangerous threats in cybersecurity.
1. A Rising Tide of Exploits
In the first half of 2025, zero-day exploits rose by 46 percent compared with the same period in 2024, according to Forescout’s Vedere Labs (Forescout, 2025). Meanwhile, Google’s Threat Intelligence Group identified 75 zero-day vulnerabilities exploited in the open in 2024, down from 98 in 2023 but still higher than 2022’s count of 63 (Dark Reading, 2024). That figure continues a multi-year upward trend in real-world exploitation (Todyl, 2025; SOC Prime, 2025; Cybersecurity Dive, 2025).
Also notable is the growing focus on enterprise systems. In 2024, 44 percent of zero-day exploits were directed at enterprise platforms, up from 37 percent in 2023. Security and networking products accounted for 60 percent of these enterprise-targeted exploits (Cybersecurity Dive, 2025; GreyNoise, 2025).
2. The Tactical Edge of Attackers
Attackers, especially state-sponsored groups, are embracing zero-day vulnerabilities for their clarity of impact. They offer undetectable entry points into sensitive systems. At the same time, financially motivated groups have shown growing interest in zero-days. For example, in 2024, nearly 15 percent of attributed zero-day exploits were linked to non-state criminal groups such as FIN11 and CIGAR, used for extortion or espionage (Google Cloud, 2025; Todyl, 2025). This duality means breaches are becoming both technically sophisticated and financially damaging.
3. High-Profile Incidents That Defined 2025
One of the most dramatic zero-day incidents in 2025 involved Microsoft SharePoint servers. By exploiting two previously unknown vulnerabilities dubbed ToolShell (CVE-2025-53770 and CVE-2025-53771), Chinese-linked actors gained access to hundreds of organizations across government, infrastructure, and private sectors (Windows Central, 2025; Reuters, 2025). The vulnerability was first disclosed in May and patched in July, but attackers quickly developed methods to bypass the update (Reuters, 2025). Microsoft responded by restricting access to its Active Protections Program for some companies, particularly those in China, removing early proof of concept code and instead offering general descriptions (Windows Central, 2025).
Another case worth noting occurred in cloud service environments. Since 2023, a Chinese-linked threat actor known as Murky Panda has exploited zero-day flaws in SaaS platforms. These flaws provided a stealthy initial access that allowed lateral movement into customer networks, demonstrating the novel risks emerging in cloud supply chain attacks (Cybersecurity Dive, 2025; TechRadar, 2025; SOC Prime, 2025).
4. What This Means for Breach Trends
Zero-day exploits are often the difference between a contained breach and a full-scale disaster. Their use is more frequent, more sophisticated, and more targeted at high-value systems than ever before.
For organizations, zero-days represent silent threats. Their detection is often delayed until after a breach is underway. Cloud supply chains and remote infrastructure add layers of complexity and expose new attack surfaces.
5. The Impact of AI on Zero-Day Exploits
Artificial intelligence is amplifying both the offensive and defensive sides of zero-day exploitation.
Acceleration of discovery and exploitation: AI-driven tools can analyze massive amounts of code and system behavior to uncover unknown vulnerabilities at unprecedented speed. Researchers have already demonstrated AI models identifying multiple zero-day bugs in widely used open-source projects (Wired, 2025). This means attackers could automate parts of the exploit discovery process that previously required skilled human effort.
Scaling attacks: AI agents can craft exploits, adapt to defenses in real time, and even launch multiple attacks simultaneously across different platforms (Wired, 2025). This lowers the barrier for less-skilled actors while increasing the scale and persistence of advanced adversaries.
AI for defense: On the flip side, defenders are using AI to spot anomalies faster and cut through the noise of false alerts. Google and Microsoft, among others, are investing in AI-assisted vulnerability hunting and patch prioritization. AI-enhanced intrusion detection systems can also recognize suspicious behavior that traditional signatures miss (Trend Micro, 2025).
The result is an arms race: AI is making zero-day discovery easier for attackers while also equipping defenders with smarter tools to detect and neutralize these threats earlier.
6. Rethinking Defense Strategies
To counter zero-day risks, defenders are shifting methods. These include:
Zero Trust frameworks that assume compromise.
Proactive threat intelligence from groups like Google Project Zero and MITRE ATT&CK.
Faster patching and anomaly detection, especially for enterprise platforms.
And a renewed focus on vendor security, secure development practices, and supply chain integrity.
Given the trends we’ve seen, from FIN11 selling zero-days to the ToolShell campaign and cloud supply chain compromises, defenders must develop proactive, layered strategies that assume zero-days are inevitable.
7. Final Word
Zero-day exploits are redefining breach landscapes around the world. They are more prevalent and used by a mix of criminal and state actors. They target infrastructure that many organizations take for granted, from SharePoint servers to third-party cloud providers. Every breach driven by zero-days reinforces the lesson that digital security cannot be reactive. It must anticipate the unseen.
Thanks for reading Rina’s Thought Of The Day! Subscribe for free to receive new posts and support my work :)

